Subject: HashiCorp Vault
In today’s digital landscape, managing secrets—such as passwords, API keys, and encryption keys—has become a critical aspect of maintaining security and operational efficiency. As organizations grow and their infrastructure becomes more complex, the challenge of secret sprawl can lead to significant security vulnerabilities and operational overhead. HashiCorp Vault is a powerful tool designed to address these challenges by providing a centralized, secure, and efficient way to manage secrets. This Q&A is tailored for individuals preparing for HashiCorp Vault interviews or exams, particularly those at a beginner level. It aims to test your comprehensive understanding of the need for secrets management, the core functionalities and features of HashiCorp Vault, and its architecture and key components. Whether you are a software developer, system administrator, or security professional, this guide will help in testing your knowledge of the essential concepts and practical applications of HashiCorp Vault, enhancing your readiness for interviews and real-world scenarios.
Learning Objectives
- Understanding the Need for Secrets Management and the Problems It Solves
- Recognize the challenges of secret sprawl and its impact on security and operational efficiency.
- Understand the concept of “secrets” in software development and system administration.
- Identify how the lack of centralized secrets management contributes to security vulnerabilities and operational overhead.
- Knowing the Core Functionalities and Features of HashiCorp Vault
- Learn how Vault utilizes encryption to protect secrets both at rest and in transit.
- Understand the concept of dynamic secrets and their advantages over static secrets.
- Explore Vault’s “encrypt as a service” capability and its role in a layered security approach.
- Understanding Vault’s Architecture and Its Key Components
- Describe Vault’s architecture, including its core, API, secret engines, storage backends, authentication methods, and audit devices.
- Explain the role of authentication backends and their integration with identity providers.
- Understand the importance of audit devices in maintaining an audit trail of secret access and their use in security analysis and compliance.
1) Learning Objective: Understanding the Need for Secrets Management and the Problems It Solves
Question 1: What are the primary challenges organizations face with secret sprawl, and how does it impact security and operational efficiency?
Answer 1: Secret sprawl creates significant challenges for organizations, including increased risk of unauthorized access, difficulty in tracking and rotating secrets, and operational inefficiencies. The lack of a centralized system makes it nearly impossible to manage secrets effectively, leading to security vulnerabilities and higher operational costs. It also hinders incident response and compliance efforts. For example, without centralized management, secrets might be stored in various locations such as code repositories, configuration files, or shared documents, making them hard to track and secure.
Question 2: Explain the concept of “secrets” in the context of software development and system administration. Provide diverse examples of secrets and their usage.
Answer 2: Secrets are sensitive pieces of information that grant access to systems or data. Examples include passwords, API keys, encryption keys, database credentials, and certificates. They’re used for authentication, authorization, and encryption to protect sensitive data and systems. In software development, secrets are used for accessing databases, APIs, and other services. In system administration, they’re used for server login, managing cloud resources, and configuring applications. For instance, an API key might be used by a web application to authenticate requests to a third-party service.
Question 3: How does the lack of centralized secrets management contribute to security vulnerabilities and operational overhead? Provide real-world examples.
Answer 3: Without centralized secrets management, organizations often store secrets insecurely (e.g., in code, configuration files, or shared documents). This increases the risk of accidental exposure, unauthorized access, and data breaches. Manually managing secrets is also inefficient, leading to increased operational overhead and difficulty in enforcing consistent security policies. A real-world example is a company storing database passwords in a shared spreadsheet, which is accidentally leaked, leading to a data breach.
2) Learning Objective: Knowing the Core Functionalities and Features of HashiCorp Vault
Question 1: How does Vault utilize encryption to protect secrets both at rest and in transit? Explain the importance of layered security in this context.
Answer 1: Vault encrypts secrets at rest using a master key, ensuring that even if the storage backend is compromised, the secrets remain protected. For data in transit, Vault uses TLS to secure communication between clients and the server. Layered security is crucial as it provides multiple defenses. If one layer is breached, other layers remain to protect the secrets.
Question 2: Explain the concept of dynamic secrets and their advantages over static secrets. How do dynamic secrets enhance security and simplify secret rotation? Discuss the operational benefits of dynamic secrets, particularly in incident isolation and minimizing service disruptions.
Answer 2: Dynamic secrets are generated on-demand and have short lifespans, unlike static secrets which are long-lived. This reduces the risk of compromise as the secrets are automatically revoked after a set period or upon request. Dynamic secrets simplify rotation and improve security by limiting the blast radius of a compromise. In incident isolation, they allow quick revocation of specific secrets, reducing service disruption. For example, a dynamic database credential can be generated for a specific application session and revoked immediately after use.
Question 3: What is Vault’s “encrypt as a service” capability, and how does it complement traditional access control mechanisms for protecting sensitive data like PII? How does this feature contribute to a layered security approach?
Answer 3: Vault’s “encrypt as a service” allows applications to encrypt and decrypt data without having direct access to encryption keys. This complements access control by adding another layer of protection. Even if an application is compromised, the attacker cannot decrypt data without going through Vault. This strengthens the overall security posture by ensuring that sensitive data remains protected even if other security measures fail.
3) Learning Objective: Understanding Vault’s Architecture and Its Key Components
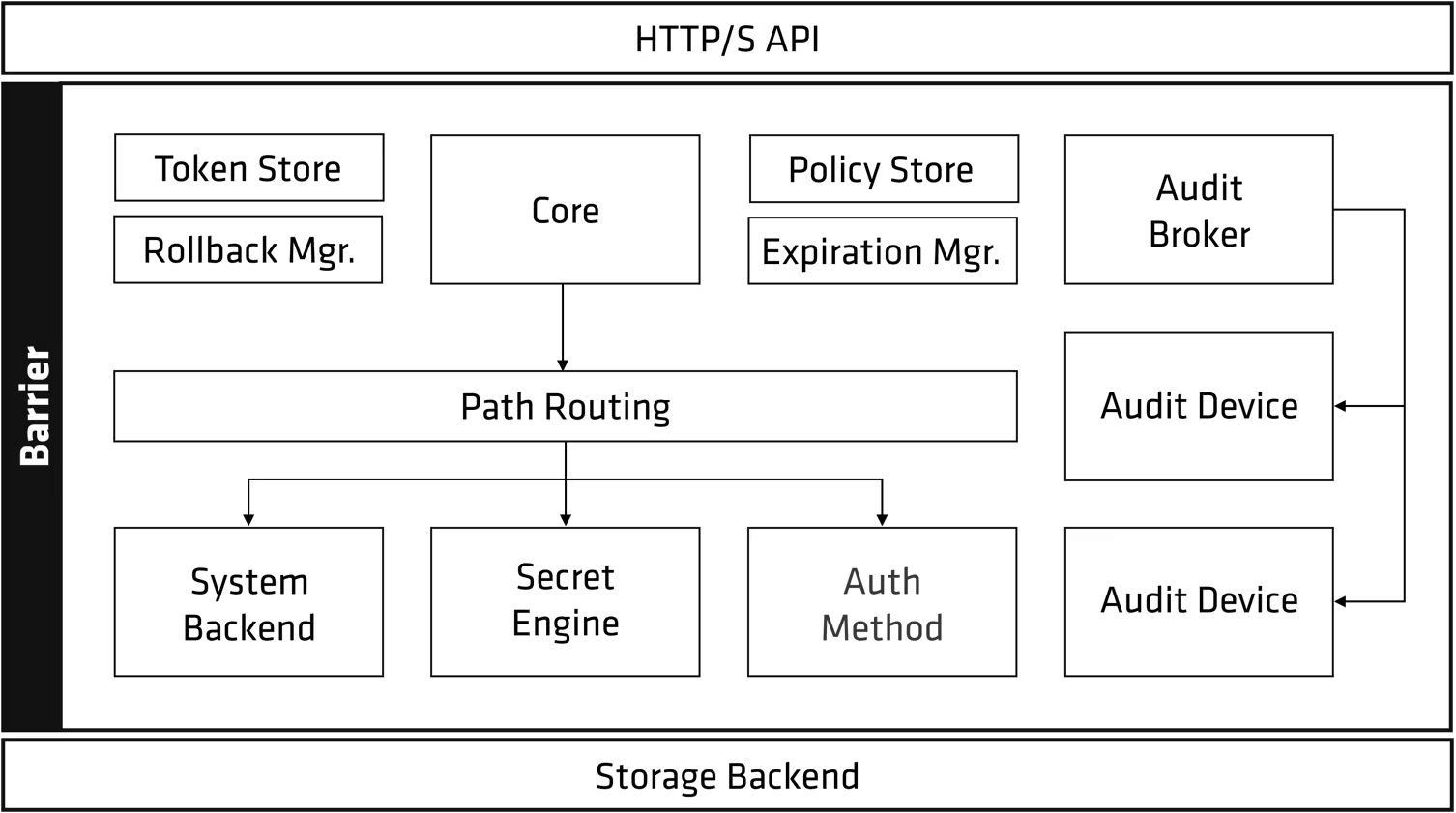
Question 1: Describe Vault’s architecture, including its core, API, secret engines, storage backends, authentication methods, and audit devices. How does this modular design contribute to Vault’s flexibility and integration capabilities?
Answer 1: Vault has a modular architecture with a central core coordinating access to secrets. Clients interact via the API. Secret engines generate and manage secrets, storage backends store encrypted data, authentication methods verify client identities, and audit devices log activity. This modularity enables flexibility and easy integration with various systems and services. For example, Vault can integrate with cloud providers for authentication and use different storage backends like Consul or AWS S3.
Question 2: Explain the role of authentication backends in Vault. How do they work in conjunction with identity providers to verify the identity of clients requesting access to secrets? Provide examples of different authentication methods and their use cases.
Answer 2: Authentication backends verify the identity of clients requesting access to Vault. They can integrate with various identity providers (like LDAP, Okta, AWS IAM) to authenticate users. Examples include username/password, tokens, Kubernetes authentication, and cloud provider integration. This allows Vault to leverage existing identity systems. For instance, Kubernetes authentication can be used to authenticate pods running in a Kubernetes cluster.
Question 3: What are audit devices in Vault, and why are they crucial for maintaining an audit trail of secret access? What kind of information is typically logged by audit devices, and how can this information be used for security analysis and compliance? Discuss the different types of audit backends and their characteristics.
Answer 3: Audit devices record every interaction with Vault, creating an audit trail of all secret access attempts (successful and failed). They log information like client IP, request details, and timestamps. This data is crucial for security analysis, intrusion detection, and compliance. Various audit backends exist, offering different storage and logging formats (e.g., file, syslog, socket). For example, a file audit device writes logs to a file, while a syslog audit device sends logs to a syslog server.
HashiCorp Vault is an essential tool for modern organizations looking to manage secrets securely and efficiently. By addressing the challenges of secret sprawl and providing robust features such as encryption, dynamic secrets, and “encrypt as a service,” Vault enhances both security and operational efficiency. Its modular architecture and integration capabilities make it a versatile solution for various environments and use cases. This Q&A has covered the fundamental concepts and functionalities of HashiCorp Vault, making it a valuable resource for beginners preparing for interviews or exams. By understanding the need for secrets management, the core features of Vault, and its architecture, you will be well-equipped to tackle questions and real-world scenarios involving HashiCorp Vault.